
Atlassian Cloud Security for the Boardroom: Managing Business Risk
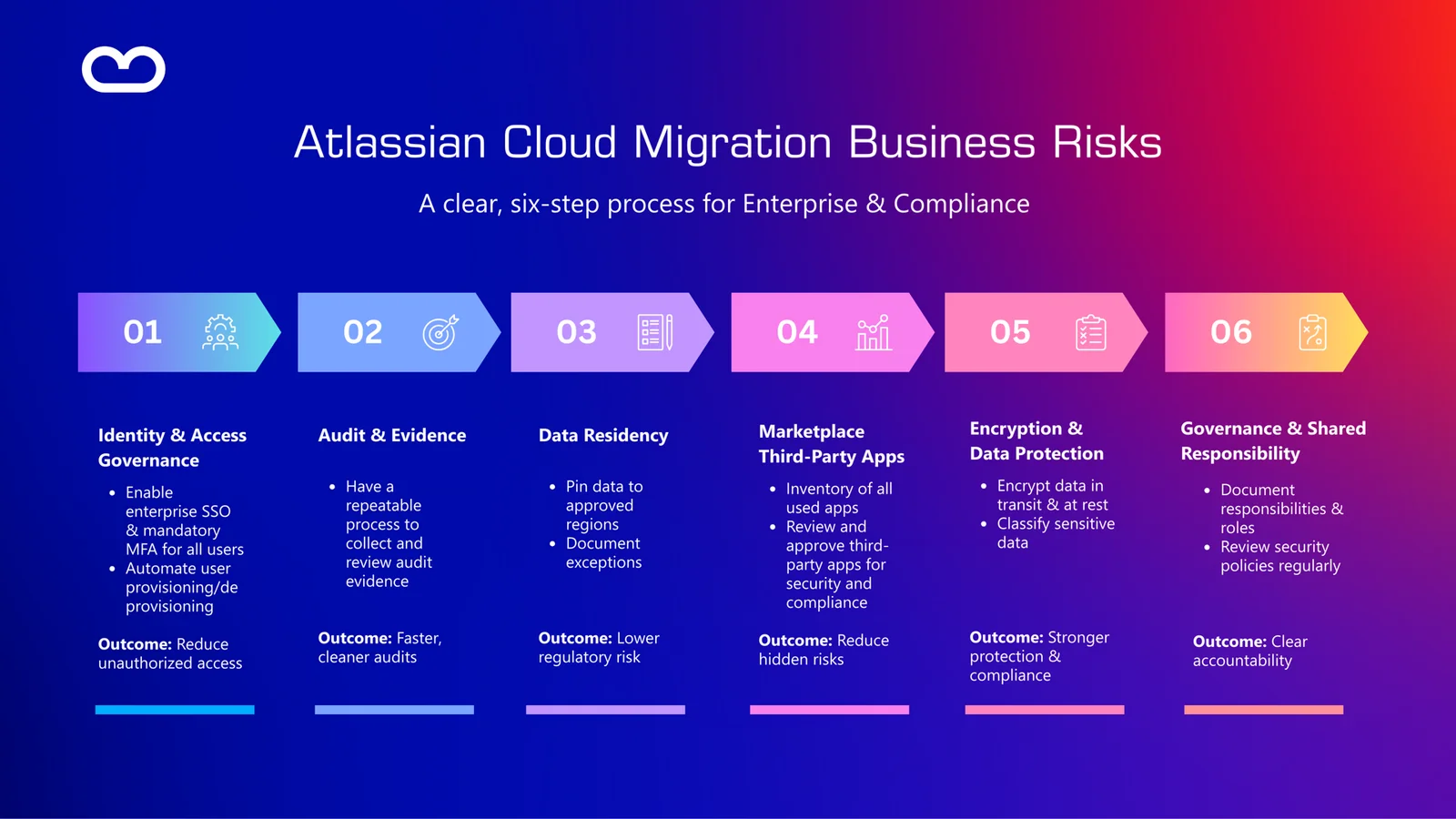
Migrating from Atlassian Data Center to Cloud changes your risk landscape: Atlassian handles infrastructure, but identity, audit, data residency, and third-party apps remain your responsibility. This guide translates technical controls into business-risk language, helping executives understand the compliance, operational, and regulatory impacts. Learn how to align Atlassian Cloud security with boardroom priorities and enterprise risk management.
For enterprise leaders, especially in highly regulated sectors like finance, security isn’t about technical controls. It’s about business risk, regulatory defensibility, and strategic resilience. Yet when organizations assess their Atlassian estate, particularly those still on Data Center, the cloud conversation often gets tangled in jargon and implementation details rather than executive risk outcomes.
This piece reframes Atlassian Cloud security as a business conversation: one that CEOs, boards, and executive teams can lead with confidence.
From Technical Risks to Tangible Business Outcomes
Traditional Atlassian Data Center environments burden internal teams with infrastructure security, patching, and compliance evidence. Risks here show up as:
- Delayed updates and unpatched vulnerabilities
- Fragmented access control enforcement
- Manual audit evidence collection processes
In finance environments, where audit cycles and controls are intensively scrutinized, such operational risk translates into compliance risk, financial penalties, and brand erosion.
Atlassian Cloud shifts a large part of infrastructure security into Atlassian’s shared responsibility model, but that does not eliminate responsibility on the enterprise side. Rather, it consolidates risk, making it more visible, measurable, and auditable… if you manage it correctly.
Instead of asking “Is the cloud secure?” leaders should ask:
“How does Atlassian Cloud change our enterprise’s risk exposure compared to Data Center?”
Simplifying Cloud Audit
In most on-premises deployments, audit evidence lives in multiple tools, exports, screenshots, and know-how. Not surprisingly, this leads to:
- Extended audit cycles
- Inconsistent evidence trails
- Increased findings or remediation scope
This is particularly acute in finance, where SOX, PCI DSS, and internal controls demand traceable user activities, access logs, and evidence of controls.
Our recent article on Top Security Mistakes in Atlassian Cloud Migration highlights that many enterprises overlook audit logging and encryption in cloud setups, often the very controls auditors require proof for.
Cloud can make audit evidence easier, but only if you build governance habits. Tools like Atlassian Guard can standardize and centralize security logs, helping move audit evidence from unreliable manual artifacts to repeatable, verifiable sources.
How Data Residency, Digital Trust, and Third-Party Apps Factor Into Risk
A cloud environment is not just about where data lives; it’s about who has legal jurisdiction over it and how it is governed.
Data Residency as a Pillar of Compliance and Trust
In this article, Data Residency: Digital Trust in Atlassian Cloud, we clearly show that modern enterprises can no longer treat data residency as a box-ticking exercise. For finance leaders, the stakes are further elevated:
- Regulatory mandates that restrict data crossing borders
- Legal obligations tied to client data custody
- Audit controls tied to where and how information is stored
Data residency is strategic, not technical. However, one under-appreciated risk comes from Marketplace app data. While Atlassian can pin core product data to a region, third-party apps often store data outside those boundaries, potentially exposing regulated data to non-compliant jurisdictions. This is a compliance risk that finance teams cannot ignore when crafting a cloud-migration risk narrative.
Communicating Cloud Risk to Non-Technical Leaders
Boards and finance executives are rarely interested in control mechanisms such as SAML or ACLs. They care about:
- Probability of unauthorized access or breach
- Time to detect and respond
- What regulators will see during the next audit
- How cloud decisions affect capital, contracts, and insurance
Translate security controls into risk outcomes, for example:
- “Centralized identity reduces the probability of credential misuse.”
- “Audit logging standardization decreases audit cycle time and findings.”
- “Data residency alignment reduces regulatory exposure in EU/US markets.”
Framing security around impact and consequence is what earns traction in the boardroom.
A Finance-Focused Look: Cloud Security as Enterprise Risk Management
Enterprise financial institutions face a unique intersection of risks:
- Regulatory scrutiny (SOX, GDPR, PCI, local banking regulators)
- Operational risk and third-party vendor management expectations
- Risk appetite frameworks tied to board risk thresholds
- Cyber insurance requirements that tie premiums to documented controls
Cloud migration offers a chance to strengthen your control environment, but planning must align with financial risk priorities:
- Map cloud controls to finance risk taxonomies:
Show how Atlassian Guard maps to detective and preventative controls in your Enterprise Risk Management framework. - Align data residency to regulatory obligations:
Demonstrate how data pinning mitigates cross-border data risk and lowers exposure to fines. - Audit readiness as a strategic asset:
Use centralized logging and evidence trails to shorten audit cycles and reduce findings. - Third-party oversight:
Develop app governance policies that include vendor risk assessments and lifecycle controls.
This financial lens turns cloud security from a technical procurement decision into a risk-mitigation strategy with measurable KPIs.
Conclusion: Cloud Security is a Business Discipline
For enterprises, especially in finance, Atlassian Cloud security should be reframed away from technology checklists and toward enterprise risk management. Tools like Atlassian Guard, data residency controls, and a disciplined approach to third-party apps are not just technical enablers; they are narrative pillars in your organization’s risk story.
Managing cloud securely is about visibility, evidence, accountability, and alignment with business outcomes. When you translate technical controls into business risk language, you empower leadership to make confident, informed decisions on your cloud transformation journey.